The highly popular OneDrive file-sharing platform by Microsoft is commonly used amongst businesses. It is also, unfortunately, the vehicle that malicious actors mimic to gain trust and ultimately, access, to business’ prized data through their employee emails. These scams are designed to steal account passwords using the survey administration tool Google Forms.
In many cases, an email arrives with a PDF file attached to a message from a seemingly- credible email address. However, instead of opening the PDF, a click takes the recipient to a site not hosted on OneDrive. Next, the site prompts the user to enter their Microsoft login credentials. The spot to enter your credentials box is actually a carefully disguised Google Form. Entering your information allows the bad actor to capture passwords and scour your accounts for data and sensitive information.
The highly concerning part of the scam is that the link and file placement are genuine seeming. A check of the site certificate shows a genuine registration to onedrive.com. The catch is that the entire page is actually just an image. Clicking to download the attachment redirects users to an inauthentic site outside of OneDrive with a login ready to steal your information. The design looks so real that it’s easy to trick users if they click.
Other file types to look out for are .doc, .ppt, .xls. These file types sent as attachments are 10 years outdated, and may be a red flag to look for when spotting a phishing email. The more secure file types and most regularly used now for O365 are .docx, .pptx, .xlsx.
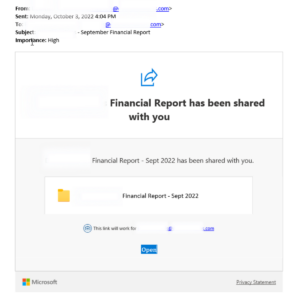
See below for a real-life example of a OneDrive phishing email described above:
So what can you do?
It is important for companies to educate their users to remember to never reply to unsolicited emails or engage with emails from unverifiable sources. If you weren’t expecting to receive an email of this nature from a sender you have communicated with about the email, reach out to that sender and confirm that they sent it prior to doing anything with or inside of the message. Additionally, forward any suspicious looking email to your IT partner for review and verification.